May 31, 2018 12:24:35 PM
Hackers, over the years, have intensified their attacks with sophisticated means sparing no means to penetrate and attack automated systems across industries.
Why attacks in the first place?
Industrial Automation Control Systems (ICS) are no exception to hackers' attempts and we have found several instances of ICS being hacked and misused. Some examples of ICS assets/technologies include SCADA (Supervisory Control and Data Acquisition), DCS (Distributed Control System), PLC (Programmable Logic Controller), data storage servers (Historian), data gateways (OPC), etc.
Vulnerabilities have affected various sectors such as the energy, manufacturing processes at multiple enterprises, water supply, and transportation as per Kaspersky Lab experts.
In June 2017, the CrashOverride/Industroyer malware was designed to disrupt the operation of industrial control systems (ICS). That same year, hackers halted oil and gas plant operations in the Middle East. In the incident, hackers used sophisticated malware to take remote control of a workstation running a shutdown system.
A question does arise: Why so many attacks in the first place?
The answer is twofold:
The cyber threat to critical infrastructure and networks is real and imminent across industries. Around 36% of companies experienced at least one operational disruption in the past two years.
The ICS used to control and manage areas such as – water management, power supply & distribution, processes in manufacturing units and oil refineries, transportation and logistics, etc., were earlier isolated from their primary business networks and used customized technologies. But now, companies with an aim to focus on efficiency and profitability are taking help of Internet technologies such as IoT resulting in the mass connectivity of all these systems making them completely vulnerable to attacks.
How do we protect the ICS from attacks?
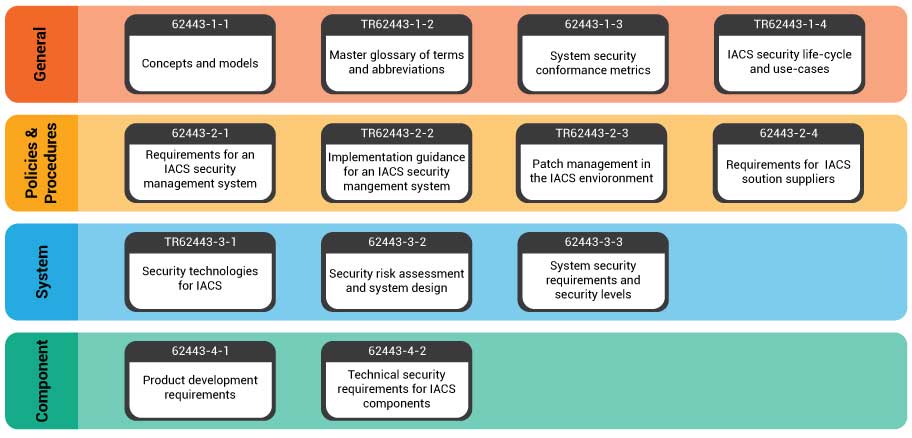
First things first, there is a need for companies to re-think their cybersecurity strategy. The ISA and IEC committee have developed series of standards (62443) to address the need to design cybersecurity robustness and resilience into industrial automation control systems (IACS). This needs to be adapted to the product development and project deployment.
So where do we begin?
Strong cybersecurity Foundation:
There is the imminent need for a robust embedded cyber security deployment model which includes securing devices & communications and security management & monitoring. A shift in the thinking process about product development from ‘everything around device/product/solution is secure' to ‘insecure' is needed.
Securing Devices:
The chain of trust and the authentication of the devices must be built up and verified from the hardware through to the software resulting in complete hardening or securing of devices. The Security starts at the physical level – with the processor within the hardware. The processor or the chip has cryptographic support, trust zone support and then build solutions like secure boot process, signed firmware and an operating system.
A proactive and holistic approach towards Cybersecurity is the only way to protect the Industrial Automation Control Systems from sophisticated hacker attacks.
Securing Communications:
Once devices are secured, secure communication spaces or channels should be secured next. Since many of the companies have legacy systems in place and it is entirely impractical to replace or revamp these immediately, the use of ‘Intelligent Gateways’ that connect legacy systems to the next-generation infrastructure systems is essential. These intelligent gateways ensure that the attack surface is minimal and the attacks are limited by physically separating production zones, legacy systems, and the outside world. The adaption of blockchain into the industrial network is the area of exploration.
Monitoring and Managing security:
ICS needs to be monitored at all times for effective management and that would be the only way to provide an overview of what is happening in the system and how it can be controlled. Enterprise management consoles allow the IT supervisors/staff to have complete visibility on the environment and monitor highly distributed environments such as the ICS. While enterprise management console allows for remote monitoring and software updates, it should also be tightly integrated with SIEM or Security Integration and Event Monitoring Solutions.
A trusted and secured environment enhances security by ensuring the devices and the communication channels do not execute malicious code. Such an environment uses encryption and virtualization technologies to create containers for data and applications that can only be accessed by authenticated devices.
Industrial control systems for an integral part of the operations of manufacturing units and with automation in tow it becomes even more essential for protecting these systems from external threats. Security at all levels, from device to communication channels to the cloud is the only way to thwart threats and keep breaches as minimal as possible.
Author: Channabasavaraj Raravi, Senior Solutions Architect – Software, Product Engineering Services
May 31, 2018 12:24:35 PM
Hackers, over the years, have intensified their attacks with sophisticated means sparing no means to penetrate and attack automated systems across industries.
Why attacks in the first place?
Industrial Automation Control Systems (ICS) are no exception to hackers' attempts and we have found several instances of ICS being hacked and misused. Some examples of ICS assets/technologies include SCADA (Supervisory Control and Data Acquisition), DCS (Distributed Control System), PLC (Programmable Logic Controller), data storage servers (Historian), data gateways (OPC), etc.
Vulnerabilities have affected various sectors such as the energy, manufacturing processes at multiple enterprises, water supply, and transportation as per Kaspersky Lab experts.
In June 2017, the CrashOverride/Industroyer malware was designed to disrupt the operation of industrial control systems (ICS). That same year, hackers halted oil and gas plant operations in the Middle East. In the incident, hackers used sophisticated malware to take remote control of a workstation running a shutdown system.
A question does arise: Why so many attacks in the first place?
The answer is twofold:
The cyber threat to critical infrastructure and networks is real and imminent across industries. Around 36% of companies experienced at least one operational disruption in the past two years.
The ICS used to control and manage areas such as – water management, power supply & distribution, processes in manufacturing units and oil refineries, transportation and logistics, etc., were earlier isolated from their primary business networks and used customized technologies. But now, companies with an aim to focus on efficiency and profitability are taking help of Internet technologies such as IoT resulting in the mass connectivity of all these systems making them completely vulnerable to attacks.
How do we protect the ICS from attacks?
First things first, there is a need for companies to re-think their cybersecurity strategy. The ISA and IEC committee have developed series of standards (62443) to address the need to design cybersecurity robustness and resilience into industrial automation control systems (IACS). This needs to be adapted to the product development and project deployment.

So where do we begin?
Strong cybersecurity Foundation:
There is the imminent need for a robust embedded cyber security deployment model which includes securing devices & communications and security management & monitoring. A shift in the thinking process about product development from ‘everything around device/product/solution is secure' to ‘insecure' is needed.
Securing Devices:
The chain of trust and the authentication of the devices must be built up and verified from the hardware through to the software resulting in complete hardening or securing of devices. The Security starts at the physical level – with the processor within the hardware. The processor or the chip has cryptographic support, trust zone support and then build solutions like secure boot process, signed firmware and an operating system.
A proactive and holistic approach towards Cybersecurity is the only way to protect the Industrial Automation Control Systems from sophisticated hacker attacks.
Securing Communications:
Once devices are secured, secure communication spaces or channels should be secured next. Since many of the companies have legacy systems in place and it is entirely impractical to replace or revamp these immediately, the use of ‘Intelligent Gateways’ that connect legacy systems to the next-generation infrastructure systems is essential. These intelligent gateways ensure that the attack surface is minimal and the attacks are limited by physically separating production zones, legacy systems, and the outside world. The adaption of blockchain into the industrial network is the area of exploration.
Monitoring and Managing security:
ICS needs to be monitored at all times for effective management and that would be the only way to provide an overview of what is happening in the system and how it can be controlled. Enterprise management consoles allow the IT supervisors/staff to have complete visibility on the environment and monitor highly distributed environments such as the ICS. While enterprise management console allows for remote monitoring and software updates, it should also be tightly integrated with SIEM or Security Integration and Event Monitoring Solutions.
A trusted and secured environment enhances security by ensuring the devices and the communication channels do not execute malicious code. Such an environment uses encryption and virtualization technologies to create containers for data and applications that can only be accessed by authenticated devices.
Industrial control systems for an integral part of the operations of manufacturing units and with automation in tow it becomes even more essential for protecting these systems from external threats. Security at all levels, from device to communication channels to the cloud is the only way to thwart threats and keep breaches as minimal as possible.
Author: Channabasavaraj Raravi, Senior Solutions Architect – Software, Product Engineering Services
Sasken is a specialist in Product Engineering and Digital Transformation providing concept-to-market, chip-to-cognition R&D services to global leaders in Semiconductor, Automotive, Industrials, Consumer Electronics, Enterprise Devices, SatCom, and Transportation industries.
Sasken Technologies Ltd
(formerly Sasken Communication Technologies Ltd)
139/25, Ring Road, Domlur, Bengaluru 560071, India
CIN# L72100KA1989PLC014226