May 2, 2025 1:11:40 PM
Security Isn’t Just for Big Systems Anymore
In a world of connected everything — from wearables and fitness trackers to smart locks and health sensors — security isn’t optional. But applying the same cryptographic methods designed for high-performance systems to tiny, low-power devices doesn’t work. These devices run on minimal memory, often have no OS, and can't afford to lose milliseconds on complex encryption routines. Yet they collect personal data. They send it wirelessly. They sit on networks. And that makes them targets.
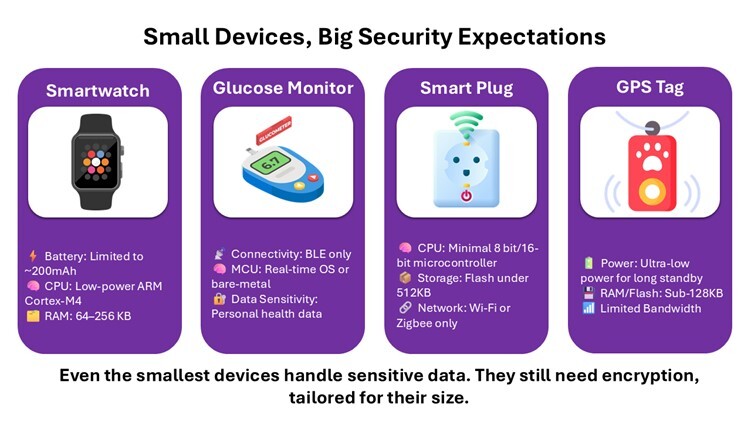
Traditional cryptography methods like RSA, ECC, or even AES (in its full-strength form) were never meant for microcontrollers with kilobytes of memory and no secure enclave. These algorithms can:
This results in an architecture dilemma: secure the device and risk lag and power loss or keep it fast and lightweight but exposed.
Lightweight cryptography is the science of developing encryption algorithms and protocols designed specifically for constrained environments. These algorithms trade off key size, rounds, or complexity — without compromising on baseline security guarantees.
Some examples include:
These are designed for fast execution on 8-bit, 16-bit, or low-end 32-bit processors. They consume less memory, need fewer cycles, and yet provide encryption, integrity, and authentication that meet industry and regulatory expectations.
Small doesn’t mean exempt. Devices that handle personal data, connect to the cloud, or support OTA updates still need to meet the Cyber Resilience Act, GDPR, HIPAA (for medical), or ISO/IEC 27001 mandates. Security must be “appropriate to the risk” — and lightweight cryptography helps meet that standard for the edge.
In fact, failing to integrate proper encryption can block certifications, delay launches, or lead to post-market recalls.
At Sasken, we work with device manufacturers, silicon vendors, and platform teams to embed lightweight security from the ground up. Our support spans:
Security is not merely about how strong your algorithms are, in fact it is also about how well they're suited to your context. For small, smart, and ubiquitous devices, lightweight cryptography is not a compromise. It’s a necessity. The goal is simple: provide just enough cryptographic muscle to meet the threat model, without draining your battery, blowing up your silicon cost, or stalling real-time operations.
At Sasken, we help you make those trade-offs wisely — and ship secure, certifiable, lightweight products that are ready for the market.
May 2, 2025 1:11:40 PM
Security Isn’t Just for Big Systems Anymore
In a world of connected everything — from wearables and fitness trackers to smart locks and health sensors — security isn’t optional. But applying the same cryptographic methods designed for high-performance systems to tiny, low-power devices doesn’t work. These devices run on minimal memory, often have no OS, and can't afford to lose milliseconds on complex encryption routines. Yet they collect personal data. They send it wirelessly. They sit on networks. And that makes them targets.

Traditional cryptography methods like RSA, ECC, or even AES (in its full-strength form) were never meant for microcontrollers with kilobytes of memory and no secure enclave. These algorithms can:
This results in an architecture dilemma: secure the device and risk lag and power loss or keep it fast and lightweight but exposed.
Lightweight cryptography is the science of developing encryption algorithms and protocols designed specifically for constrained environments. These algorithms trade off key size, rounds, or complexity — without compromising on baseline security guarantees.
Some examples include:
These are designed for fast execution on 8-bit, 16-bit, or low-end 32-bit processors. They consume less memory, need fewer cycles, and yet provide encryption, integrity, and authentication that meet industry and regulatory expectations.
Small doesn’t mean exempt. Devices that handle personal data, connect to the cloud, or support OTA updates still need to meet the Cyber Resilience Act, GDPR, HIPAA (for medical), or ISO/IEC 27001 mandates. Security must be “appropriate to the risk” — and lightweight cryptography helps meet that standard for the edge.
In fact, failing to integrate proper encryption can block certifications, delay launches, or lead to post-market recalls.
At Sasken, we work with device manufacturers, silicon vendors, and platform teams to embed lightweight security from the ground up. Our support spans:
Security is not merely about how strong your algorithms are, in fact it is also about how well they're suited to your context. For small, smart, and ubiquitous devices, lightweight cryptography is not a compromise. It’s a necessity. The goal is simple: provide just enough cryptographic muscle to meet the threat model, without draining your battery, blowing up your silicon cost, or stalling real-time operations.
At Sasken, we help you make those trade-offs wisely — and ship secure, certifiable, lightweight products that are ready for the market.