Jun 16, 2025 5:33:10 PM
Automotive security is moving beyond gateways. It is moving towards in-vehicle cybersecurity and embedded safety detection. While traditional automotive security measures such as central locking systems or secure key management still stand crucial for safety, vehicle platform architects and VSOC managers are moving towards security by design. This blog delves deeper into why and how modern vehicles and ECU firmware teams are turning toward in-vehicle cybersecurity through intrusion detection and prevention systems.
As vehicles evolve into rolling data centers, with over millions of lines in code, multi-domain ECUs, and continuous connectivity, their attack surface grows with every new feature. Automotive OEMs and Tier-1s shifting towards secure-by-design SDVs and are not limited to software defined vehicles. Rajiv Mody, CMD and CEO, Sasken Technologies, recently shared his insight into this shift. He mentioned, “Modern vehicles are significantly more exposed to cyber threats than they were a decade ago. With over 100 million lines of code, multiple wireless interfaces, cloud connectivity, and over-the-air updates, today’s cars are essentially computers with wheels. The systems, which were once isolated, like infotainment, telematics, advanced driver assistance systems (ADAS), and powertrain, have become a part of a broader system.” This shift is encouraging OEMs to expand their In-vehicle cybersecurity capabilities and not solely rely on perimeter defenses or passive compliance documentation. To truly secure a vehicle, cybersecurity must move inside the ECU, onto the vehicle network, and into the runtime memory. Our experts realize the gravity of this shift. After months of collaborating with industry leaders and experts, brainstorming with our global engineering team, we built an automotive cybersecurity solution that detects intrusion in real-time. The solution is designed specifically for modern E/E architectures and engineered to operate in production environments without disrupting critical functions. CTA: Curious to know more about Sasken’s IDPS Solution? Reach out to our experts today!
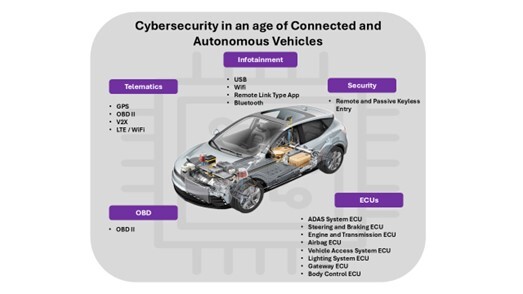
This is this In-Vehicle IDPS system like a smart home security system but for your car’s brain. Just like a smart home security system monitors doors, and detects motion in the house, our in-vehicle IDPS monitors every touchpoint in your vehicle’s electronic control system (ECS). This lightweight, embedded security system resides in the ECS environment in real-time at the application and memory level. It is capable of:
This system is built keeping in mind global compliance standards and is compliant with ISO/SAE 21434, UNECE R155, and AUTOSAR Classic & Adaptive security architecture principles. The solution is already in production deployment with global OEMs and Tier 1 suppliers, demonstrating its maturity, scalability, and effectiveness in real-world automotive environments. As vehicle platform architects, cybersecurity leaders, and VSOC managers, we understand your priority for robust and field-tested architecture. Keeping this in mind, our experts enable customers with a top-tier managed Vehicle Security Operations Center (vSOC) service that complements the IDPS, enabling continuous threat detection, monitoring, and response.
“Cybersecurity is not merely closing gaps in the code running inside the vehicle, rather it is a practice that needs to be adopted right from the conceptualization phase of the product. However, early mitigation is essential, where “security by design” must be implemented from the initial phases. This includes having security controls starting from the concept and design stages.” Continued Rajiv. Traditional automotive security approaches rely heavily on perimeter-level defenses, primarily at the gateway. Once past the gateway, lateral movement into unmonitored ECUs becomes possible. Sasken’s In-Vehicle IDPS assures:
Our value is not just in detection algorithms, it lies in our ability to make IDPS deployable, efficient, and certifiable within complex vehicle platforms.
ECU-Level IntegrationSasken’s IDPS offer includes structured support for:
We act as both your engineering integrator and compliance co-pilot.
Sasken’s IDPS approach doesn’t just stop at deploying an agent. We ensure that it's optimized, tested, validated, and integrated into the vehicle lifecycle, from development and diagnostics to updates and decommissioning. With growing regulation and rising attack sophistication, having in-vehicle visibility, real-time protection, and compliance-ready infrastructure is essential for any player in the automotive value chain.
Jun 16, 2025 5:33:10 PM
Automotive security is moving beyond gateways. It is moving towards in-vehicle cybersecurity and embedded safety detection. While traditional automotive security measures such as central locking systems or secure key management still stand crucial for safety, vehicle platform architects and VSOC managers are moving towards security by design. This blog delves deeper into why and how modern vehicles and ECU firmware teams are turning toward in-vehicle cybersecurity through intrusion detection and prevention systems.
As vehicles evolve into rolling data centers, with over millions of lines in code, multi-domain ECUs, and continuous connectivity, their attack surface grows with every new feature. Automotive OEMs and Tier-1s shifting towards secure-by-design SDVs and are not limited to software defined vehicles. Rajiv Mody, CMD and CEO, Sasken Technologies, recently shared his insight into this shift. He mentioned, “Modern vehicles are significantly more exposed to cyber threats than they were a decade ago. With over 100 million lines of code, multiple wireless interfaces, cloud connectivity, and over-the-air updates, today’s cars are essentially computers with wheels. The systems, which were once isolated, like infotainment, telematics, advanced driver assistance systems (ADAS), and powertrain, have become a part of a broader system.” This shift is encouraging OEMs to expand their In-vehicle cybersecurity capabilities and not solely rely on perimeter defenses or passive compliance documentation. To truly secure a vehicle, cybersecurity must move inside the ECU, onto the vehicle network, and into the runtime memory. Our experts realize the gravity of this shift. After months of collaborating with industry leaders and experts, brainstorming with our global engineering team, we built an automotive cybersecurity solution that detects intrusion in real-time. The solution is designed specifically for modern E/E architectures and engineered to operate in production environments without disrupting critical functions. CTA: Curious to know more about Sasken’s IDPS Solution? Reach out to our experts today!

This is this In-Vehicle IDPS system like a smart home security system but for your car’s brain. Just like a smart home security system monitors doors, and detects motion in the house, our in-vehicle IDPS monitors every touchpoint in your vehicle’s electronic control system (ECS). This lightweight, embedded security system resides in the ECS environment in real-time at the application and memory level. It is capable of:
This system is built keeping in mind global compliance standards and is compliant with ISO/SAE 21434, UNECE R155, and AUTOSAR Classic & Adaptive security architecture principles. The solution is already in production deployment with global OEMs and Tier 1 suppliers, demonstrating its maturity, scalability, and effectiveness in real-world automotive environments. As vehicle platform architects, cybersecurity leaders, and VSOC managers, we understand your priority for robust and field-tested architecture. Keeping this in mind, our experts enable customers with a top-tier managed Vehicle Security Operations Center (vSOC) service that complements the IDPS, enabling continuous threat detection, monitoring, and response.
“Cybersecurity is not merely closing gaps in the code running inside the vehicle, rather it is a practice that needs to be adopted right from the conceptualization phase of the product. However, early mitigation is essential, where “security by design” must be implemented from the initial phases. This includes having security controls starting from the concept and design stages.” Continued Rajiv. Traditional automotive security approaches rely heavily on perimeter-level defenses, primarily at the gateway. Once past the gateway, lateral movement into unmonitored ECUs becomes possible. Sasken’s In-Vehicle IDPS assures:
Our value is not just in detection algorithms, it lies in our ability to make IDPS deployable, efficient, and certifiable within complex vehicle platforms.
ECU-Level IntegrationSasken’s IDPS offer includes structured support for:
We act as both your engineering integrator and compliance co-pilot.
Sasken’s IDPS approach doesn’t just stop at deploying an agent. We ensure that it's optimized, tested, validated, and integrated into the vehicle lifecycle, from development and diagnostics to updates and decommissioning. With growing regulation and rising attack sophistication, having in-vehicle visibility, real-time protection, and compliance-ready infrastructure is essential for any player in the automotive value chain.