May 2, 2025 11:37:57 AM
The inevitable disruption is ahead.
Quantum computing isn’t a far-future theory anymore, it’s a fast-approaching reality. While today’s machines aren’t cracking RSA or ECC in practice, the theoretical groundwork already exists. As research scales and hardware matures, widely used cryptographic algorithms will become vulnerable. And when that tipping point arrives, there won’t be time to react, only regret for not preparing earlier.
“The Global Quantum Cryptography Market size is expected to be worth around USD 22.7 Billion by 2033, from USD 1.4 Billion in 2023.”
(Market.us, Tajammul Pangarkar)For industries where long product lifecycles, OTA updates, and distributed architecture are the norms—like automotive, telecom, satellite communications, and industrial systems—the stakes are especially high. The cryptographic algorithms you use today to secure communications, authenticate devices, and sign firmware may soon be broken in hours by a quantum machine.
At Sasken, we believe transitioning to post-quantum cryptography (PQC) is a fundamental shift in how secure products are designed and operated. But this transition is neither simple nor instant. It requires a careful balance of performance, interoperability, and long-term resilience.
At a glance, post-quantum cryptography might seem like a problem for CISOs, compliance teams, or government agencies. But it directly impacts engineering decisions at the hardware, software, and system architecture level and thus sits squarely on the radar of product managers, firmware architects, system integrators, and DevOps leads. Across industries, these teams are asking the same questions:
These are complex challenges, and the transition to PQC won’t happen overnight. A well-planned, potentially hybrid cryptographic approach is needed to ensure both security and interoperability.
The first critical reason is longevity. Unlike consumer software that updates frequently, products in automotive, telecom, industrial, and satellite environments often stay in the field for 10+ years. Any cryptographic decisions made today must be able to withstand future quantum threats, even if those threats become practical only five years from now. Waiting until PQC is mandated will create a massive retrofit burden: revalidating hardware, redesigning firmware signing flows, retesting OTA systems, and possibly even re-certifying products.
Second, regulatory pressure is catching up. The U.S. National Institute of Standards and Technology (NIST) has already announced four PQC algorithm finalists (like Kyber and Dilithium), and standards are imminent. The European Union’s Cyber Resilience Act (CRA) indirectly addresses post-quantum cryptography by mandating that digital products and services must be secure against current *and future* threats. Whether or not your current market demands PQC today, your next one likely will, especially if you’re shipping to the EU or working with connected or safety-critical systems.
Engineering, product, compliance, and security teams need to align early to avoid silos and rework. For example, if PQC introduces boot time overhead, performance tuning must be coordinated between firmware and platform teams. If new algorithms impact device provisioning or secure manufacturing, DevOps and production teams must be looped in.
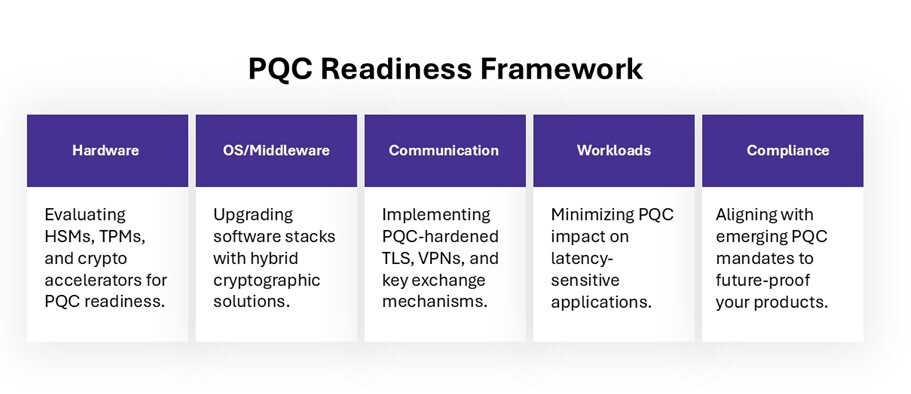
Post-quantum algorithms like Kyber and Dilithium (both finalists in NIST’s PQC standardization) demand more from your hardware than legacy schemes. PQC algorithms require more processing power than traditional encryption. Key sizes are larger. Signature verification takes longer. And operations often exceed what's optimized in today’s TPMs, HSMs, or embedded secure elements.
Here’s what must be evaluated:
For embedded products, especially those with tight power, space, and thermal budgets, the answer may not be straightforward. This is why hardware audit and crypto profiling need to be the first step.
Integrating new cryptographic algorithms means updating crypto libraries, middleware, bootloaders, and container orchestration logic, without breaking existing functionality.
The key challenges include –
Many secure communication protocols rely on asymmetric cryptography for key exchange and authentication—protocols like TLS, SSH, VPN tunnels, and 5G authentication mechanisms.
Performance will be a concern. Key exchange with PQC can take longer and increase handshake size. That impacts latency-sensitive systems in automotive and telecom where real-time guarantees matter.
Systems like autonomous vehicles, 5G core networks, and industrial control systems are deeply sensitive to cryptographic overhead. Even minor latency increases can affect performance, safety, or user experience. How will this impact latency-sensitive applications? Will be a primary concern for these industries.
Regulators have already begun moving. NIST’s post-quantum standards are finalizing. ENISA has released industry guidance. Automotive standards and EU-wide mandates like the Cyber Resilience Act (CRA), AI Act, are already influencing how security needs to be embedded and maintained across the product lifecycle.
Sasken brings together 30+ years of experience across embedded systems, device platforms, telecom stacks, and secure product engineering. We support end-to-end PQC integration through:
Multi-Layered Offerings:
The quantum threat is no longer abstract. The timeline may not be exact, but the direction is clear. Whether you're securing next-gen vehicle platforms, building 5G infrastructure, or deploying industrial devices, crypto-agility is the new baseline. Besides security, it’s design, performance, and go-to-market decision. Start now, while you can plan smartly, do not react fast.
Let’s get your products quantum-safe, together.
May 2, 2025 11:37:57 AM
The inevitable disruption is ahead.
Quantum computing isn’t a far-future theory anymore, it’s a fast-approaching reality. While today’s machines aren’t cracking RSA or ECC in practice, the theoretical groundwork already exists. As research scales and hardware matures, widely used cryptographic algorithms will become vulnerable. And when that tipping point arrives, there won’t be time to react, only regret for not preparing earlier.
“The Global Quantum Cryptography Market size is expected to be worth around USD 22.7 Billion by 2033, from USD 1.4 Billion in 2023.”
(Market.us, Tajammul Pangarkar)For industries where long product lifecycles, OTA updates, and distributed architecture are the norms—like automotive, telecom, satellite communications, and industrial systems—the stakes are especially high. The cryptographic algorithms you use today to secure communications, authenticate devices, and sign firmware may soon be broken in hours by a quantum machine.
At Sasken, we believe transitioning to post-quantum cryptography (PQC) is a fundamental shift in how secure products are designed and operated. But this transition is neither simple nor instant. It requires a careful balance of performance, interoperability, and long-term resilience.
At a glance, post-quantum cryptography might seem like a problem for CISOs, compliance teams, or government agencies. But it directly impacts engineering decisions at the hardware, software, and system architecture level and thus sits squarely on the radar of product managers, firmware architects, system integrators, and DevOps leads. Across industries, these teams are asking the same questions:
These are complex challenges, and the transition to PQC won’t happen overnight. A well-planned, potentially hybrid cryptographic approach is needed to ensure both security and interoperability.
The first critical reason is longevity. Unlike consumer software that updates frequently, products in automotive, telecom, industrial, and satellite environments often stay in the field for 10+ years. Any cryptographic decisions made today must be able to withstand future quantum threats, even if those threats become practical only five years from now. Waiting until PQC is mandated will create a massive retrofit burden: revalidating hardware, redesigning firmware signing flows, retesting OTA systems, and possibly even re-certifying products.
Second, regulatory pressure is catching up. The U.S. National Institute of Standards and Technology (NIST) has already announced four PQC algorithm finalists (like Kyber and Dilithium), and standards are imminent. The European Union’s Cyber Resilience Act (CRA) indirectly addresses post-quantum cryptography by mandating that digital products and services must be secure against current *and future* threats. Whether or not your current market demands PQC today, your next one likely will, especially if you’re shipping to the EU or working with connected or safety-critical systems.
Engineering, product, compliance, and security teams need to align early to avoid silos and rework. For example, if PQC introduces boot time overhead, performance tuning must be coordinated between firmware and platform teams. If new algorithms impact device provisioning or secure manufacturing, DevOps and production teams must be looped in.
Post-quantum algorithms like Kyber and Dilithium (both finalists in NIST’s PQC standardization) demand more from your hardware than legacy schemes. PQC algorithms require more processing power than traditional encryption. Key sizes are larger. Signature verification takes longer. And operations often exceed what's optimized in today’s TPMs, HSMs, or embedded secure elements.
Here’s what must be evaluated:
For embedded products, especially those with tight power, space, and thermal budgets, the answer may not be straightforward. This is why hardware audit and crypto profiling need to be the first step.
Integrating new cryptographic algorithms means updating crypto libraries, middleware, bootloaders, and container orchestration logic, without breaking existing functionality.
The key challenges include –
Many secure communication protocols rely on asymmetric cryptography for key exchange and authentication—protocols like TLS, SSH, VPN tunnels, and 5G authentication mechanisms.
Performance will be a concern. Key exchange with PQC can take longer and increase handshake size. That impacts latency-sensitive systems in automotive and telecom where real-time guarantees matter.
Systems like autonomous vehicles, 5G core networks, and industrial control systems are deeply sensitive to cryptographic overhead. Even minor latency increases can affect performance, safety, or user experience. How will this impact latency-sensitive applications? Will be a primary concern for these industries.
Regulators have already begun moving. NIST’s post-quantum standards are finalizing. ENISA has released industry guidance. Automotive standards and EU-wide mandates like the Cyber Resilience Act (CRA), AI Act, are already influencing how security needs to be embedded and maintained across the product lifecycle.
Sasken brings together 30+ years of experience across embedded systems, device platforms, telecom stacks, and secure product engineering. We support end-to-end PQC integration through:
Multi-Layered Offerings:

The quantum threat is no longer abstract. The timeline may not be exact, but the direction is clear. Whether you're securing next-gen vehicle platforms, building 5G infrastructure, or deploying industrial devices, crypto-agility is the new baseline. Besides security, it’s design, performance, and go-to-market decision. Start now, while you can plan smartly, do not react fast.
Let’s get your products quantum-safe, together.