Apr 28, 2025 4:29:59 PM
The Trade-Offs Are Real
Security isn’t an add-on anymore. It’s part of how products are evaluated, certified, and trusted in today’s world. But integrating security into system architecture often comes with tough questions. As product leaders, engineering architects, and compliance owners, you face this dilemma regularly:
These aren’t hypothetical concerns. In sectors like automotive, telecom, industrial, and IoT, the wrong architectural decisions can lead to data leaks, regulatory violations, or costly product recalls.
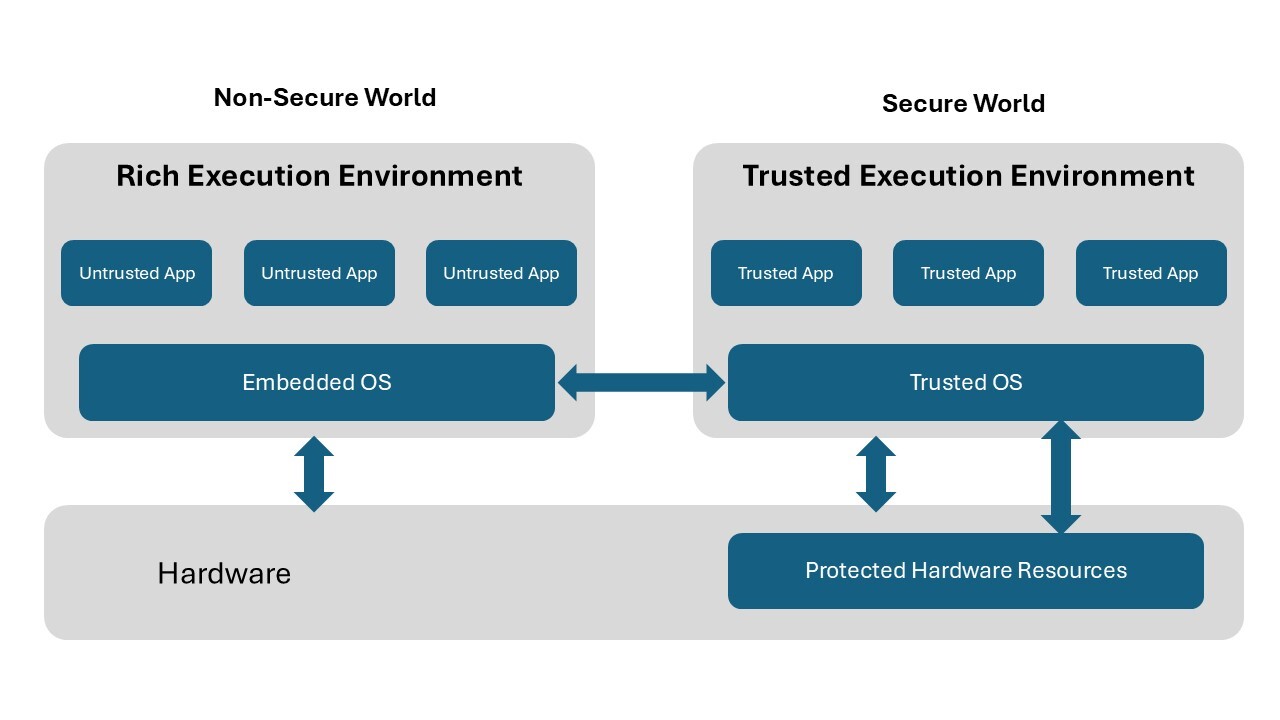
This is the standard Linux or Android environment used in most connected devices. It provides full functionality, supports third-party software, and is easy to update. But it also brings baggage – large attack surfaces, dependency vulnerabilities, and risks of privilege escalation.
A Secure Enclave is a hardware-isolated section of the processor that runs code independently of the main OS. Even if the Rich OS is compromised, the workloads inside the enclave stay protected. It could be considered a vault inside your device, ideal for sensitive data and operations.
The question becomes: what goes where?
ML models, especially ones embedded in edge devices, carry high intellectual property (IP) value. Hosting them in a Rich OS makes them vulnerable to extraction, reverse engineering, or adversarial attacks. Using a Secure Enclave adds a layer of confidentiality, protecting model weights, decision logic, and runtime data.
Security telemetry is only as good as its integrity. If an attacker tampers with logs or detection modules running in the Rich OS, your threat response may be blind. Isolating key threat monitoring components in a TEE ensures logs and analytics stay trustworthy.
Secure boot mechanisms verify the integrity of firmware and OS at startup. These roots of trust should never be exposed. Keeping boot keys and validation logic in a secure enclave hardens the system against malware injected at the bootloader or kernel level.
Regulations like UNECE WP.29, ISO/SAE 21434, and the EU’s Cyber Resilience Act require demonstrable controls around data confidentiality, secure software updates, and auditability. A secure-by-design approach that uses isolated execution environments supports this by design.
We understand that getting secure architecture right is about balancing trade-offs — security, performance, cost, and compliance. At Sasken, we help customers navigate these decisions with:
Security is about making smart architectural choices early in the design process. As attack vectors grow and compliance becomes stricter, knowing where your workloads run is as important as knowing what they do.
The best systems are built to resist them by design.
Are your products architected for compliance, resilience, and security-by-design?
Apr 28, 2025 4:29:59 PM
The Trade-Offs Are Real
Security isn’t an add-on anymore. It’s part of how products are evaluated, certified, and trusted in today’s world. But integrating security into system architecture often comes with tough questions. As product leaders, engineering architects, and compliance owners, you face this dilemma regularly:
These aren’t hypothetical concerns. In sectors like automotive, telecom, industrial, and IoT, the wrong architectural decisions can lead to data leaks, regulatory violations, or costly product recalls.

This is the standard Linux or Android environment used in most connected devices. It provides full functionality, supports third-party software, and is easy to update. But it also brings baggage – large attack surfaces, dependency vulnerabilities, and risks of privilege escalation.
A Secure Enclave is a hardware-isolated section of the processor that runs code independently of the main OS. Even if the Rich OS is compromised, the workloads inside the enclave stay protected. It could be considered a vault inside your device, ideal for sensitive data and operations.
The question becomes: what goes where?
ML models, especially ones embedded in edge devices, carry high intellectual property (IP) value. Hosting them in a Rich OS makes them vulnerable to extraction, reverse engineering, or adversarial attacks. Using a Secure Enclave adds a layer of confidentiality, protecting model weights, decision logic, and runtime data.
Security telemetry is only as good as its integrity. If an attacker tampers with logs or detection modules running in the Rich OS, your threat response may be blind. Isolating key threat monitoring components in a TEE ensures logs and analytics stay trustworthy.
Secure boot mechanisms verify the integrity of firmware and OS at startup. These roots of trust should never be exposed. Keeping boot keys and validation logic in a secure enclave hardens the system against malware injected at the bootloader or kernel level.
Regulations like UNECE WP.29, ISO/SAE 21434, and the EU’s Cyber Resilience Act require demonstrable controls around data confidentiality, secure software updates, and auditability. A secure-by-design approach that uses isolated execution environments supports this by design.
We understand that getting secure architecture right is about balancing trade-offs — security, performance, cost, and compliance. At Sasken, we help customers navigate these decisions with:
Security is about making smart architectural choices early in the design process. As attack vectors grow and compliance becomes stricter, knowing where your workloads run is as important as knowing what they do.
The best systems are built to resist them by design.
Are your products architected for compliance, resilience, and security-by-design?